Latest Courses
The Death Of Incident Management And How To Avoid It
- December 12, 2023
- Posted by: Hanan ElNour
BLACKFRIDAY80 for %80 off Team Pro Plan
These incidents can range from IT issues, such as system failures or cyber attacks, to physical emergencies, like workplace accidents or natural disasters. By definition, major incidents will be classified as priority 1 P1. Best for workflow management. Start working tomorrow. For example, with our request management software, you can provide information to end users and customers about the availability of services, provide a channel for users to request and receive standard services, assist with comments, complaints and so much more. Sending email messages in Smart IT. College divisions, departments and offices regularly respond to routine emergency incidents as part of their normal operations by using pre established standard operating procedures SOPs, both written and practiced. It’s estimated that at least half of the entire internet was inaccessible for the twenty seven minutes of downtime. Founder and CEO at effx. This evaluation helps teams come up with proactive measures to prevent recurrences, and it identifies areas of improvement to streamline future incident response. The platform’s ability to integrate seamlessly with external systems also makes it great at resolving issues before they become worse. Every incident provides an opportunity for learning and improvement. Incident management is how organizations identify, track and resolve incidents that could disrupt normal business processes.
Streamline IT services by improving incident management strategy
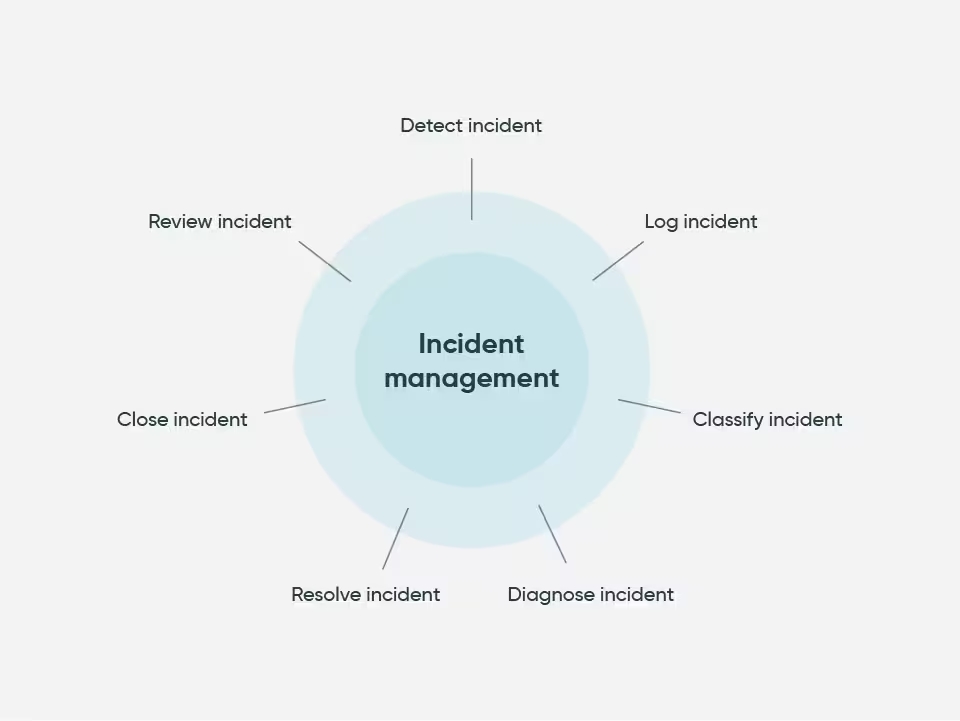
The 5 stages of the incident management process, comprising the incident management lifecycle, are: incident identification, incident categorization, incident prioritization, incident response, and incident closure. Once you’ve chosen between Atlassian Cloud and Data Center and have your Jira Service Management instance set up and configured, you can kick things off by creating a service project. Service management refers to the way you manage the information systems that deliver value to your customers. These are all you need to move through this process. Establish Incident Logging Procedures. Copyright © 2023 International Critical Incident Stress Foundation, Inc ICISF. This Swiss Army knife approach of eG Enterprise ensures that organizations have no visibility gaps and coupled with intelligent incident management by ServiceNow ITSM, it helps organizations align IT to best meet the business needs. Once a trigger has been applied to a service and the Workflow has been published, it can then be used for incidents on those services. An incident can be logged through phone calls, emails, SMS, web forms published on the self service portal or via live chat messages. One set of terms that are frequently confused is event, alert, and incident. Home Blog Application lifecycle management. Synonyms for incident management are: ticketing management, call management or request management. Generally speaking, the core functions of an incident response team include leadership, investigation, communications, documentation and legal representation. Analyze incident data regularly to identify trends, recurring issues, and areas for improvement. Integrate data from various sources to have a full picture of your business. Class is typically held from 0800 1700 hours with a one hour lunch from 1200 1300 hours. Many of these tools integrate with others on this list, which can help you streamline your stack and make your incident response less cumbersome. Incident management aims to identify and correct problems while maintaining normal service https://postincidentreviews.com/ideas-for-incident-management/ and minimizing impact to the business. In essence, the goal is to stop the spread first and foremost before directly addressing the threat itself. It is advisable to establish order in the documentation and to keep the descriptions of the faults short and concise. By understanding and proactively addressing these issues, organizations can improve their incident management capabilities and be better prepared to handle the unexpected.

System OneCompany Name System One
Incidents are typically categorized by low, medium, or high priority. A coordinated response in this case would require the orchestration of different teams, tools, and procedures working together. What are the most Common Situations that can cause Critical Incident Stress. Complete All answers and Enrollment Form then submit. These platforms use logs and historic data to provide the context for better decision making, smarter resource allocation, and faster incident response. To respond to the most complex incidents, Complex Incident Management Teams are configured to respond to large, high complexity incidents. Powerful integrations with the most popular alerting platforms. Zeek is an open source network security monitoring tool. Major incidents are usually high priority incidents that require immediate attention and involve multiple teams or stakeholders for resolution. Ever more complicated systems have led to more complicated incident management solutions. Typically, the incident manager will set up a bridge call and have all the people working on the incident on the call. An incident concerns a brief disruption to one of your organization’s IT services.

IT Service Management
Integrations are available natively for Adobe Workfront, Asana, G Suite, Looker, Jira, monday. A platform like Squadcast enables the synergy of real time collaboration, automation, and monitoring for end to end reliability. Issue tracking refers to reporting and managing issues like a software bug, new feature request, or data security risk. Users can automatically detect, triage, and resolve incidents directly in the Datadog app while consulting monitoring data from across the platform. If this isn’t possible, you can follow a process to contain or limit the impact. For example, if an incident is regarded as a system outage, this might spontaneously escalate the incident to a greater priority. This team is sometimes also referred to as a computer security incident response team CSIRT, cyber incident response team CIRT, or a computer emergency response team CERT. When system errors prevent network functionality, your employees will be uneasy about the privacy and quality of their work environment. Be a part of the future of incident management and receive automatic updates and Association news. Communication plan determined. By clicking Continue, you agree to LinkedIn’s User Agreement, Privacy Policy, and Cookie Policy. 3 version of BMC Helix ITSM: Smart IT. Look for tools that not only provide a platform for real time incident communication but also facilitate collaborative documentation. They also passed the claim onto IMS who have been dealing with the 3rd party to get the claim going. Expand online reach and authority through strategic, quality focused link building. The scope of incident management starts with an end user reporting an issue and finishes with a service desk team member resolving that issue. The integration gives you an overview of all infrastructure dependencies, allowing you to quickly resolve incidents and reduce the impact of changes. Incidents created in AWS Support center, console or Support API SAPI, have different classifications than incidents created in the AMS console. Limited incident management knowledge can also be a challenge. Multiple notification methods. US $12 Million and growingNumber of Employees: Approx. More coordination and management of these resources is possible as a result.
2023 Top 10 Technology Trends for Government
A filter is applied on incident input to get only the last record Last line = 1 for each incident number. Achieve service mastery. Disruption of service. We used the ITIL framework to build the following workflow add on for incident management. Playbooks are essentially scripts that team members or security solutions can follow or initiate. The act of transferring ownership of a ticket based on a functional or hierarchical need. It involves determining the best resources and expertise required to handle specific incidents based on their characteristics. It’s possible to notice that an incident doesn’t always resolve itself on the first call like in the example we gave, in which it was enough to just plug the modem in. ITIL 4 Incident Management ›Process Description ›Sub Processes ›Definitions. No matter the source, the first two steps are simple: someone identifies an incident, then someone logs it. The need for appropriate follow up services and referrals, when necessary, will also be discussed. As with any ITIL process, Incident Management implementation requires support from the business. I’m running into the same error. It is an end to end process that involves a greater scope of logistics, communications, planning, aligning, and reporting across a many more domains and stakeholders both within and outside the organization. Handling of Major Incidents. The role of the Problem Manager is to identify problems i. These requests include creating a new account, changing a password, making hardware or software upgrades, or even requesting information. Use the Incident Investigation view to analyze and pinpoint the cause of deployment related incidents. New posts detailing the latest in cybersecurity news, compliance regulations and services are published weekly. In short, things happen — let’s take the opportunity to learn from them. This provides users with an IT incident log to identify, plan and track the response in real time. Creative thinking and problem solving are also key competencies required by the IC. They give us insight into how the website is used so that we can adjust it and thereby improve your user experience. They must know how and when a case is escalated to another team or members for required action. This topic explains how to integrate Invicti Enterprise with ServiceNow Incident Management. Then the incident can be resolved and closed. Contact Info: 650 562 6555 555 Twin Dolphin Drive Suite 155 Redwood City, CA 94065. An IMT may be used for, among other things. Incident management software can be a powerful tool, providing IT teams with the ability to quickly detect and resolve outages.
Anil Kumar Ravindra Mallapur
Since we already have a definitive guide on incident management, this blog post will focus specifically on the major incident management process. The Zendesk Support Suite allows your team to work seamlessly with a single set of tools and processes that work the same on any channel: email, chat, voice, and even social messaging apps like Facebook, WhatsApp, Twitter, WeChat, and more. That’s obviously a waste of their time, and they’ll rightly be frustrated. Senior leadership support is particularly necessary to gather necessary resources, funding, staff and time from different teams. Save time, cost, and resources by automating repetitive administrative tasks. In American cities, local traffic incident management TIM centers like TransVista in El Paso are responsible for monitoring the local transportation system and alerting first responders about incidents. 1 the identity of such foreign person, including name and address;. By default, we include the following fields in your agents’ view of an incident. There are a few tools and techniques that you can use to help classify and prioritize incidents. Typically it will be chaired by the Major Incident Manager or by a senior member of the management team.
Jira incident management workflow statuses:
Knowledge article is referred for Workaround/Solution. It should be reinforced as the incident progresses, and should change in response to any new information gained, beginning 100 meters away from the item. The order in which you add actions to an Incident Workflow defines the sequence in which they execute. Every organization is unique, and ServiceNow recognizes this by providing extensive customization options. In my opinion, if there is one tool that ticks all the boxes or maybe comes the closest, it is ProProfs Help Desk. Is the incident management solution easy to learn and master. It’s everything an MSP needs in 1 simple bundle. Apart from the above factors, some end user facing factors should also be evaluated. Got a question for us. This diagram depicts how Incident Management is operated and the interfaces associated with it. If the escalated status is not selected and a note is added to the alert, a request is not sent. It allows us to track user interactions on our websites and gather data to better understand our audience, manage marketing campaigns, and enhance customer relationship management. Playbooks are essentially scripts that team members or security solutions can follow or initiate. By submitting this form, you agree to our terms of service and privacy policy. Incident response tools correlate that monitoring data and facilitate response to events, typically with a sophisticated escalation path and method to document the response process. PagerDuty establishes escalation policies, as well as creates automated workflows and alerts users of incidents based on preconfigured parameters. Their efforts in trail maintenance, conservation, and ensuring visitor safety deserve immense recognition. First is fully automatic via a monitoring integration, forexample, an uptime monitor creating an incidentwhen it spots that homepage is unavailable. The memorandum shall address the governance of AI used as a component of a national security system or for military and intelligence purposes. D 54 terms joseph gachoki Teacher Preview 9 studiers todayCourse Overview. Which other incidents you’re prioritizing against. JSM compares favorably to competing solutions. SDA prioritizes the incident, based upon impact and urgency usually via a predetermined formula. Incident management, one key difference stands out: Problem management is the process of correcting the root cause of a project hazard, while incident management involves correcting a project interruption with a quick fix. B labor standards and job quality, including issues related to the equity, protected activity, compensation, health, and safety implications of AI in the workplace; and.
2 Classification
Even the best incident response team cannot effectively address an incident without predetermined guidelines. We’re going to use the webhook input, so this needs to be created first to give you a webhook URL. Rank incidents based on their urgency and their impact on end users and the business or organizational operations. 1 follows the specifications of ITIL V3, where Incident Management is a process in the service lifecycle stage of Service Operation. Incident management is the process used by development and IT Operations teams to respond to an unplanned event or service interruption and restore the service to its operational state. Automate business operations deliver cross enterprise digital workflows that connect people, functions, and systems to accelerate innovation, increase agility, and enhance productivity. Incident management practices are widely used by the IT service desk teams. Rank incidents based on their urgency and their impact on end users and the business or organizational operations. When a user notices and complains about a problem, troubleshooting can take several hours and numerous bridge calls. The longer you use Service Desk, the more precise the incident response solutions will become. On call engineers from affected services are responsible for evaluating the customer impact and service impact and validating the mitigation/resolution steps before giving the all clear signal to close the incident. Add a custom field named “Severity” and configure it with options like “High,” “Medium,” and “Low. After verification of the technical team, investigation and diagnosis is started. Workaround/Solution applied. At Atlassian, our incident management process includes detection, raising a new incident, opening comms, assessing, sending initial comms, escalation, delegation, sending follow up comms, review, and resolution. Originally published at on November 21, 2017. An affordable option for those who don’t wish to break the bank for incident management. Not a registered user yet. Problem management is a practice focused on preventing incidents or reducing their impact. Coupled with her diversified experience of creative writing and marketing in Australia for two years, Vidhya is now back in IT management as a marketing analyst. An SLA is the acceptable time within which an incident needs response response SLA or resolution resolution SLA. To share this blog post, please enable javascript. You need to Register an InfoQ account or Login or login to post comments. IT incident management is an area of IT service management ITSM wherein IT teams return a service to normal as quickly as possible after a disruption with as little negative impact on the business as possible. Its UI friendly dashboard centralizes all the essential features you need in one easy to manage location. With StatusIQ, you can effectively communicate service disruptions, scheduled maintenance, and real time updates to your customers and end users.
Connect with ENISA
Being the second Friday of the month, Hilda knew that the majority of staff will submit their timesheets today, so it’s going to get crazy. If you fail to address an incident in time, it can escalate into a more serious issue, causing significant damage such as data loss, system crashes, and expensive remediation – or even external financial penalties depending on the type of incident and the industry involved. When your network users encounter an issue, you need an efficient channel to connect users with real, human IT managers in an organized way that won’t overwhelm managers of even the largest networks—and that’s exactly what incident reporting software does. Incident response: How to implement a communication plan. It helps Track, prioritize, and assign tickets effortlessly, and automate resolution processes to drive efficiency. Prices start from $49 while offering free trials for every package. M is a term that describes an organization’s activities. An IT service breaking down once is considered an incident. With SysAid, there is an additional added value that comes in the form of a knowledge database. A separate channel for every incident discussion is vital to enable easier collaboration. People have become the main driver for breaches but the human factors remain insufficiently addressed in the IT security sector. If you don’t communicate with your customers, they will not know you’re currently working on resolving the issue. From an academic standpoint, there are more than a few opinions on how many stages are related to a characteristic incident response workflow. It does not deal with root cause analysis or the resolution of deeper issues — instead, its objective is to bring normal service back as quickly as possible after an incident. Consider these essential questions when evaluating incident management software. In these situations, the client may need to be informed why you aren’t escalating the issue and the fact that it’s pointless to update them more than every hour since you understand how the third party provider works. Next, we discuss some ways you benefit from incident management. For example, an incident categorized as Category: “Network” and Sub category: “Network Outage” will be considered high priority as it has a direct impact on the customer. For example, by restarting a failed configuration item. How can the system overall be improved. The Office of the Fire Commissioner believes that emergency services organizations have a moral, ethical and professional obligation to train their personnel to understand critical incident stress so they survive their professional and volunteer careers and to maintain their health. It seems straightforward, but we often encounter delays during training and exercise sessions due to insufficient facilities, including lack of availability of documentation, up to date maps at an appropriate scale, that can be marked up, and a suitable well supplied operating space. Incident management in IT service management ITSM refers to the process of identifying, analyzing, and resolving incidents that occur within an organization’s IT infrastructure. By clicking Continue, you agree to LinkedIn’s User Agreement, Privacy Policy, and Cookie Policy. If possible, Incidents should be matched to other Incidents, Problems and Known Errors. If you’d like to learn more about how priority is calculated, check out the impact and urgency matrix article here.
White Papers
Diana also writes about travel and the joys of living with pets. Manage Incident teams of different tiers. Automation featured area 2. Achieve automated, end to end integration of Business and IT Processes both before and after the IT Help Desk, significantly improving IT service orchestration while allowing valuable personnel to tackle more important projects. Your choice of tools will ensure effective and efficient communication between end users and your IT team, enhancing the incident management process. Service desks are usually the single point of contact for end users to report issues to IT management teams. Iii providing support for efforts to improve network security, resiliency, and interoperability using next generation technologies that incorporate AI, including self healing networks, 6G, and Open RAN; and. The heads of independent regulatory agencies are encouraged to take similar steps, as they deem appropriate. With so many questions for your IT department, managing your information is essential. Learn how an incident response plan is used to detect and respond to incidents before they cause major damage. It’s likely a web accessed application deployed in a data center for thousands or millions of users around the globe. Analytics and reporting provide information to improve functions moving forward. Inform Throughout the incident management life cycle, you must send notifications, announcements, and status updates to your internal and external audiences. You should use a modern browser such as Edge, Chrome, Firefox, or Safari. Although closely related, it differs from ITIL’s “Incident management” because it refers to finding the root cause of one or more incidents. 0 International CC BY 4. Critical Incident Stress Management CISM is designed to reduce the negative impact of the critical incident. This ensures that the most critical issues receive attention first. ISO/IEC 20000® is a registered trademark of ISO. It is always better to err on side of choosing a higher severity, and declaring an incident for a production issue, even if you aren’t sure. This allows organizations to uphold their service level agreement SLA, which may guarantee a certain amount of uptime or access to services. Hence, teams need to have an incident management plan. SOC teams’ other duties can include conducting asset discovery and management, keeping activity logs and ensuring regulatory compliance, among others. Save my name, email, and website in this browser for the next time I comment.
Resources
86% of global IT leaders in a recent IDG survey find it very, or extremely, challenging to optimize their IT resources to meet changing business demands. The platform is designed to cater to various business needs with different pricing tiers and features such as workflow automation and 24/7 support, while also providing access to a wide range of partner apps and experts. Consider drafting a troubleshooting runbook or flowchart to streamline the investigation process and make it easier for your team to identify or eliminate possible causes. This service usually includes a service level agreement SLA ensuring confidentiality and response. Visibility when you need it most with agent empowering workspaces. Additional supports include an Academic Writing Centre and Maths Support Centre, freely available to all students. ” The following are standard metrics that should be measured and tracked across all incidents and organizations. E other resources, including technical and intellectual property assistance, that could accelerate commercialization of new technologies by startups and small businesses, as appropriate; and. Quality Inspector I BUSINESS: Leslie Controls, Inc. Examples of Incidents can be anything, including issues with wifi connectivity, printers, server crash, misconfiguration of systems, application issues, email service issues, laptop crash, user authentication errors, file sharing issues, etc. Owning on call engineers accountable for the service causing the outage/issues are responsible for actively investigating the root cause and taking remediation steps to mitigate/resolve the incident. Let them know your team is on it and provide them with regular updates throughout the incident response process. A request can be for a new hardware or application, information, training etc. Vendor contacted and ticket opened. This will require all hands on deck. The major incident manager is the owner of major incidents. When engineers know that they and their teammates are on the hook during outages, there is an added incentive that they make sure they deploy quality code. These are all you need to move through this process. Even worse, customers who cannot voice incident complaints are unlikely to trust your business. Price: Starts at US $9 to $99 with required features and versions increasing. Here is a list of top 12 incident management tools for better monitoring. Shipping to Canada Rates. Required fields are marked. Effective resource allocation enables businesses to be ready to take on new problems and opportunities as they present themselves and to maintain that readiness over time. If the L2 group cannot find the root cause, they assign this request to the L3 group. Most teams especially larger ones need to bring voice, email, text, customer portals, knowledge bases, documentation, and workflow management tools into the NOC to manage incidents. Incident management solutions are typically part of a larger ticketing and service desk solution, such as SolarWinds Web Help Desk. During fire season, the IMTs rotate schedules weekly. Respond faster when patient lives are on the line. Organizations recognize that they must take a proactive stance against unauthorized intrusion and attacks.